Overview - CodeShield
Find and fix cloud attack paths before an adversary exploits them
CodeShield uncovers how attackers can abuse vulnerabilities and over-privileged IAM policies to move within your cloud and reach your critical assets - it’s basically an automated whitebox pentest of your AWS environment.
Get up and running in minutes
CodeShield is agent-less and connects directly to the cloud provider's API. Its integration is seamless and does not impact any assets running in your (production) account. CodeShield uses an agent-less setup to connect to your AWS account using the sts:AssumeRole technology by AWS. The setup deploys a role within your AWS account, which allows CodeShield to access the required information. The setup takes less than a couple of minutes.
Want to get started? Check out the QuickStart.
CodeShield’s cloud model and IAM privilege escalations
CodeShield uses the cloud’s API to generate a cloud access and data-flow model. Based on the model, CodeShield detects IAM privilege escalation vulnerabilities. An IAM privilege escalation vulnerability is a new type of cloud vulnerability for which an attacker combines IAM policies to gain unintended access over your cloud.
Example Privilege Escalation
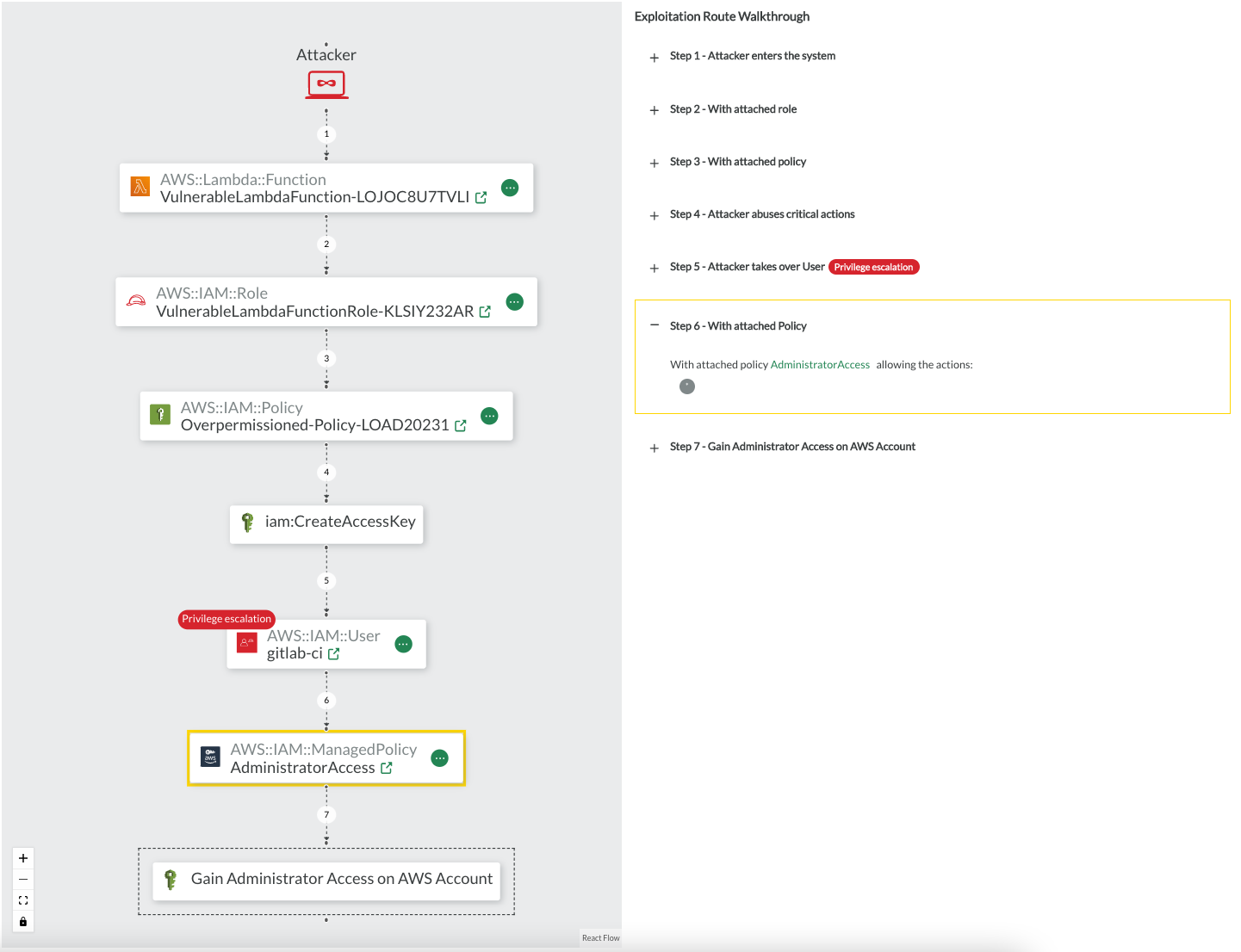
CodeShield describes potential attack scenarios based on privilege escalation. An example is found the screenshot below.
In the example, assume an attacker gained control over the AWS Lambda function
VulnerableLambdaFunction-LOJOC8U7TVLI, for instance, by exploiting an existing vulnerability of your code dependencies (CVE) or a vulnerability in the Lambda's custom code. The Lambda function has a role attached with a policy that comprises a critical action. The actioniam:CreateAccessKeygenerally allows to create access keys for users within the AWS account. As the Lambda has the permission to execute the action, the Lambda itself can create access keys for arbitrary users. The account also contains agitlab-ciuser, which has the managed policyAdministratorAccessattached. Consequently, an attacker can abuse the vulnerable Lambda function to create a new access key for thegitlab-ciuser, log in as that user, and, compromise the entire AWS account.
Cloud hacks and potential attacks
There are many more goals an attacker is interested in, such as spawning EC2 instances to run ransomware or exfiltrate critical data. CodeShield’s team continuously researches to maintain a complete set of privilege escalation methods and attack goals, and maps the goals to the official MITRE ATT&CK® Cloud Matrix. Hereby, CodeShield continuously provides you with an overview of your current cloud security posture from an attacker's point of view.